Who We Are
Our goal is to ensure you can operate and grow your business with the peace of mind knowing your data, entities, and knowledge are safe and secure 24x7, 365. We believe in a “Win-Win” philosophy – your success is our success! Being customer-centric ensures that we put you first in everything we do from our daily operations to how we conduct business with our partners. This allows us to make sure that you are given a quality experience when working with us. We conduct business ethically and respectfully and we believe that trust is the foundation in any business partnership.
PBS PhantomWatch employs cyber and information security methodologies designed to assess the triad of people, processes, and technologies. Additionally, our project management and customer service is second to none. We help protect your business with industry-leading solutions, managed security services, and cyber expertise. Our team members consist of passionate highly certified security practitioners and thought leaders that continuously share forward thinking and innovative ideas. It’s this collaborative environment that allows our experts to keep your organization safe from today’s cybersecurity threats.
Get StartedManaged Security Offerings
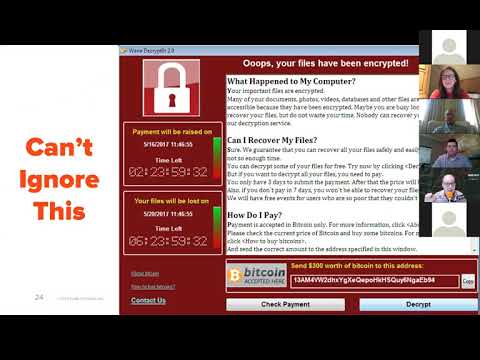
As the cyber threat landscape becomes increasingly more sophisticated, finding a way to protect network data, systems, and applications has become a top priority for most businesses. PBS PhantomWatch’s Managed Security Offerings provides a proactive and cost-effective solution for organizations to protect, detect and respond to cybersecurity threats, 24 hours a day, 365 days a year.
PhantomWatch SOC
PhantomWatch brings experienced people, proven process, and industry leading technology to continually protect, detect, respond, and recover from cyber threats across the ADIS environment.
Watch VideoSOC Intakes Data
• Network Security Firewall
• Endpoint Security (PC/VDI)
• Model Security
• SPAM and Email Security
• Data Loss Prevention (DLP)
• SaaS Application Security
• Identity Access Mgmt (IAM)
• Multi-Factor Authentification (MFA)
• Server, Network, & Application Logs
• Network Flows and Packet Data
• Cloud Access Security Broker (CASB)
• Internet of Things (IoT)
SOC Provides
• Automated Response
Capability to Address
Security Incidents
• Remediation Guidance /
Incident Response
• Security Tuning
and Improvement
Recommendations
• Regular Security Status and
Compliance Reporting
• Monthly Security Briefings
Implement Improvements Utilizing
• Solution Tuning
• Process Improvements
• Technology Changes
• User Training
• Other Actions
Find Out How We Can Provide Security to Your Business